Security Alert: Simple Google Queries Uncover Sensitive Government Documents

Most people who spend a good bit of time online know that you can do special additions to your searches to help Google find what you want - things like adding quotes around your search to find an exact phrase or specifying a timeframe.
But even still, we have trouble finding exactly what we’re looking for - often because we don’t know how to ask.
And that’s where really understanding search operators can make a huge difference. Even beyond quotes and timeframes, you can use search operators like filetype: or site: to help Google understand your specific intent.
Google’s ability to decipher your intent matters, which is why search operators are more than just a fun tool for SEOs to play with. They can help you evaluate contracts by tracking down comparables, reconnect with old friends that don’t have a presence on standard social platforms, or even just find a very specific piece of content from a very specific source.
To demonstrate, I’d like to pose a question:
What would be the most difficult thing to find with Google?
How about sensitive US government documents? Those have to be locked down and buried, right? After all, Federal spending on IT security runs about $6 billion dollars per year.
Contractors with USB drives notwithstanding, let’s see if we can harness the power of search operators and Google to try to find sensitive & “for official use only” government documents.
The Search
First, we’ll make an educated guess that the Department of Homeland Security will have some interesting documents, so we’ll use the query site:dhs.gov “secret government documents” to start.
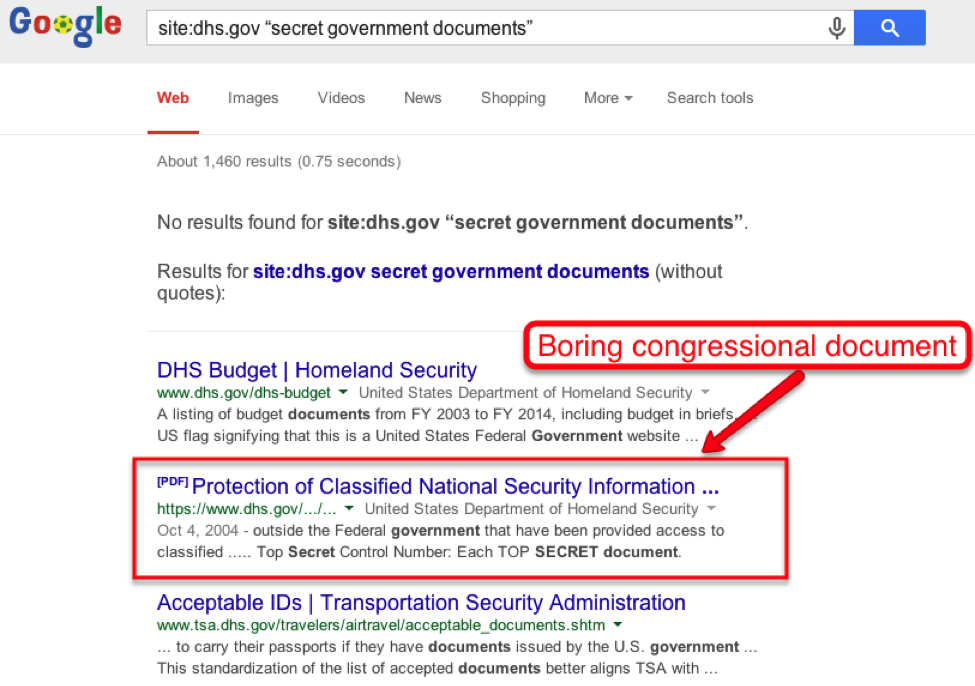
Okay, so Google isn’t really understanding what I want. There’s nothing called “secret government documents.” Also, Google doesn’t recognize that phrase as a topic so it’s serving related results about DHS documents. However, if the DHS is going to have a sensitive document online, it’s probably not going to be a webpage - it’ll be an actual document. So let’s look at all the PDFs with the query site:dhs.gov filetype:pdf
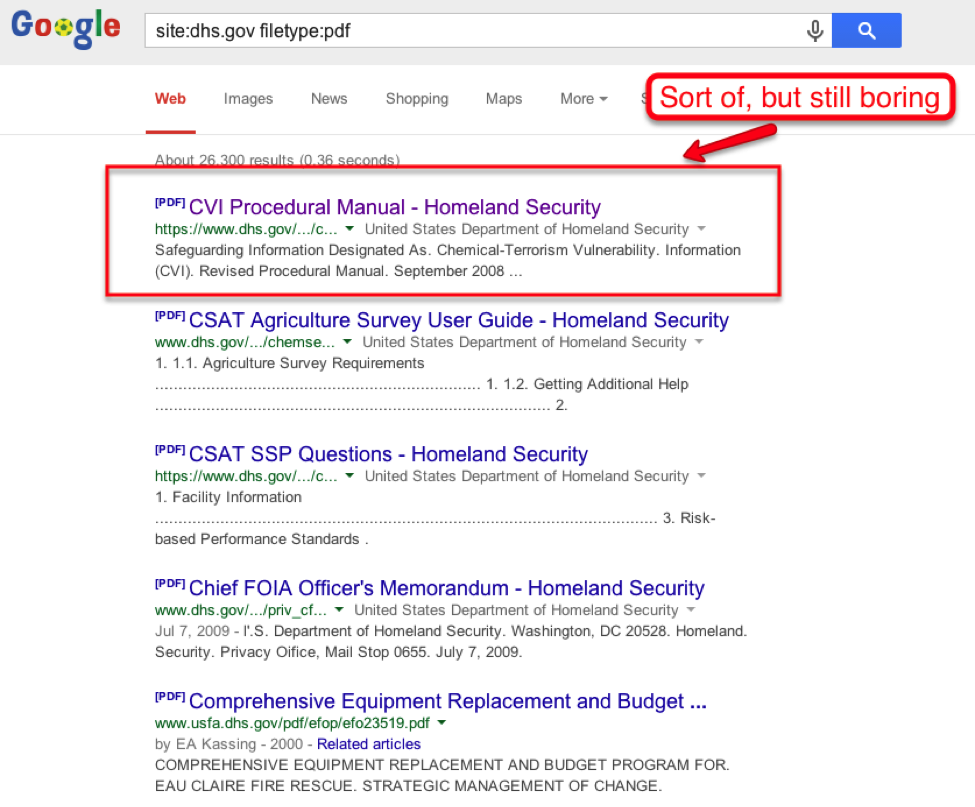
Now we’re getting somewhere. But there are still 26,300 documents to sort through. Let’s try adding a phrase that would only appear in a sensitive or classified document with filetype:pdf site:dhs.gov classified
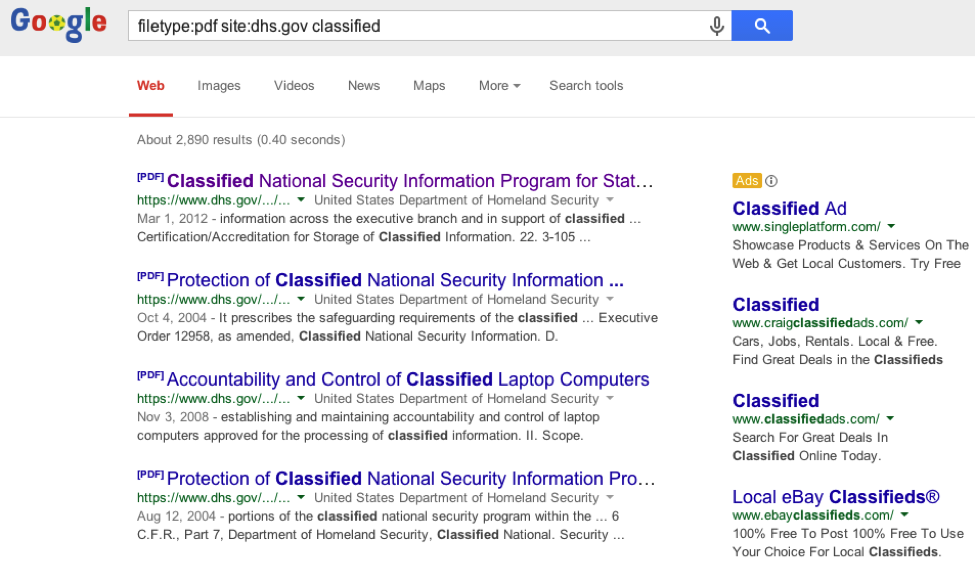
Getting closer - we now only have 2,890 documents to sift. But note how Google understands “classified” to be an adjective rather than a document type. It’s a subtle difference, but still key.
We’re going to have to do a couple things. First, we’ll use negative keywords like -classification to filter some documents and add another phrase that would only appear in the actual text of a sensitive document such as intext:”for official use only”
Add all that up and we have our final query - filetype:pdf intext:"For Official Use Only" classified -classification -unclassified site:dhs.gov to plug into Google.
Sensitive Government Documents
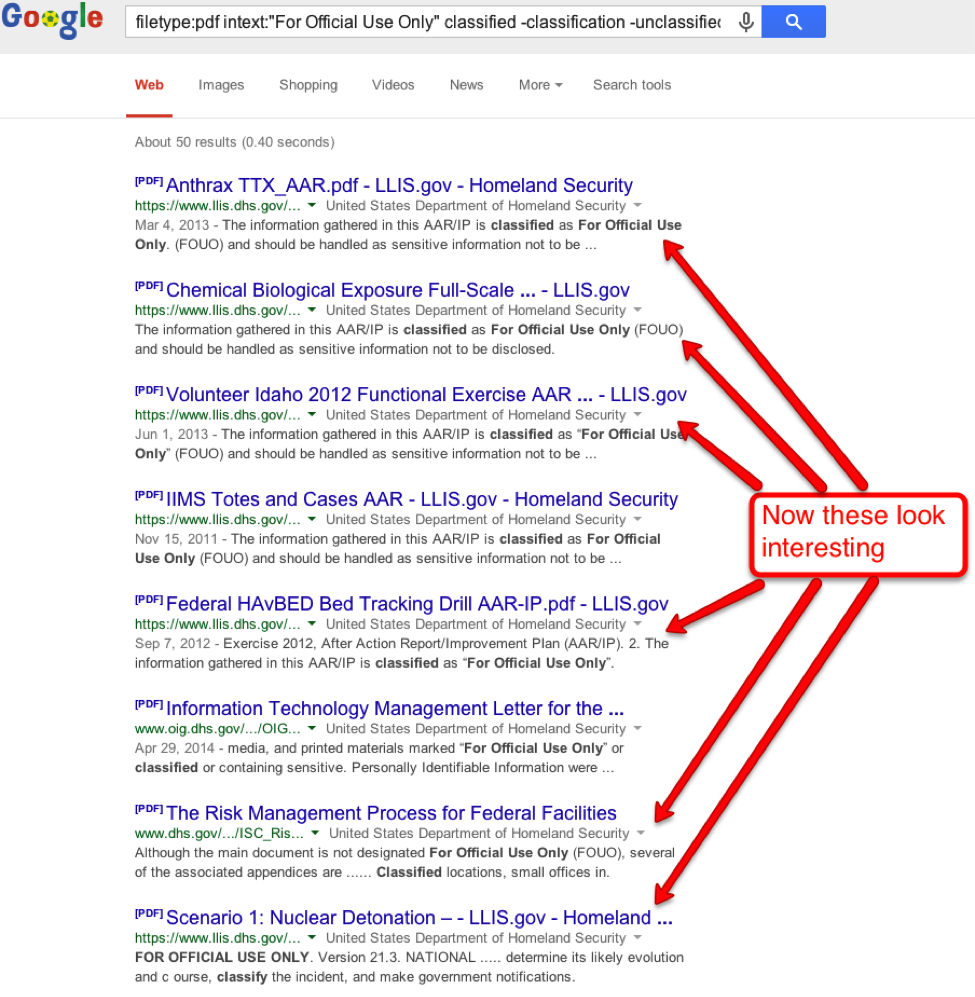
Now we have 50 documents, most of which look very interesting.
Disclaimer: Just because these are findable via Google does not mean it’s a good idea to download them. So don’t do that.
Also, once this post is published, hopefully the Federal government will spend a portion of our $6 billion dollar IT security budget to apply a NOINDEX tag to these documents. But for fun and exploration, here’s a sampling of what you can find.
Walking Dead fans will be interested in the Maryland Strategic National Stockpile Operations Exercise Report at:
Which notes that:

Hmm. That’s really not cool that you can find this with a Google search.
Next up, you can take a look at the White Powder Anthrax Tabletop Exercise Report.
https://www.llis.dhs.gov/sites/default/files/Anthrax%20TTX_AAR.pdf

And it doesn't make me very comfortable to know that our Chemical or Biological weapons attack response plans are public at -

Not all the documents available are shocking or on the same level as PRISM findings from Edward Snowden, but they are documents which probably shouldn’t be accessible with a Google search.
Even mundane documents like the Customs & Border Patrol Use of Force policy isn’t something that Taliban, a Mexican drug cartel...or really anyone should be able to just Google.
http://www.dhs.gov/sites/default/files/publications/cbp-use-of-force-policy.pdf

And all these results are just from the site:dhs.gov website. Change the site: operator to dod.gov (the home of the US Department of Defense) and search for:
filetype:pdf intext:"For Official Use Only" classified -classification -unclassified site:dod.gov
And you find things like the Bush-era enhanced interrogation training manuals:
http://www.dod.gov/pubs/foi/operation_and_plans/Detainee/PREAL%20Operating%20Instructions.pdf

Conclusion
Whether you are looking for sensitive government documents or the perfect dinner recipe, Google Search is a tool, and it’s most effective when you know how to help it help you. You can start learning search operators by finding the full list here and then just testing it out on Google Search.
Lastly, if you run a government agency, please place a NOINDEX on all non-public files and password protect the directory.
Comments
Add A CommentThis is for the remember how we can keep the particular setting for the computer. This type of the tools use for the make good connectivity and easily operations in the windows 10 sync settings greyed out.
Very interesting what explain and already found a way as to be applied to my project. Thanks